Amber Group has fixed a second security lapse that exposed private keys and passwords for the government’s JamCOVID app and website.
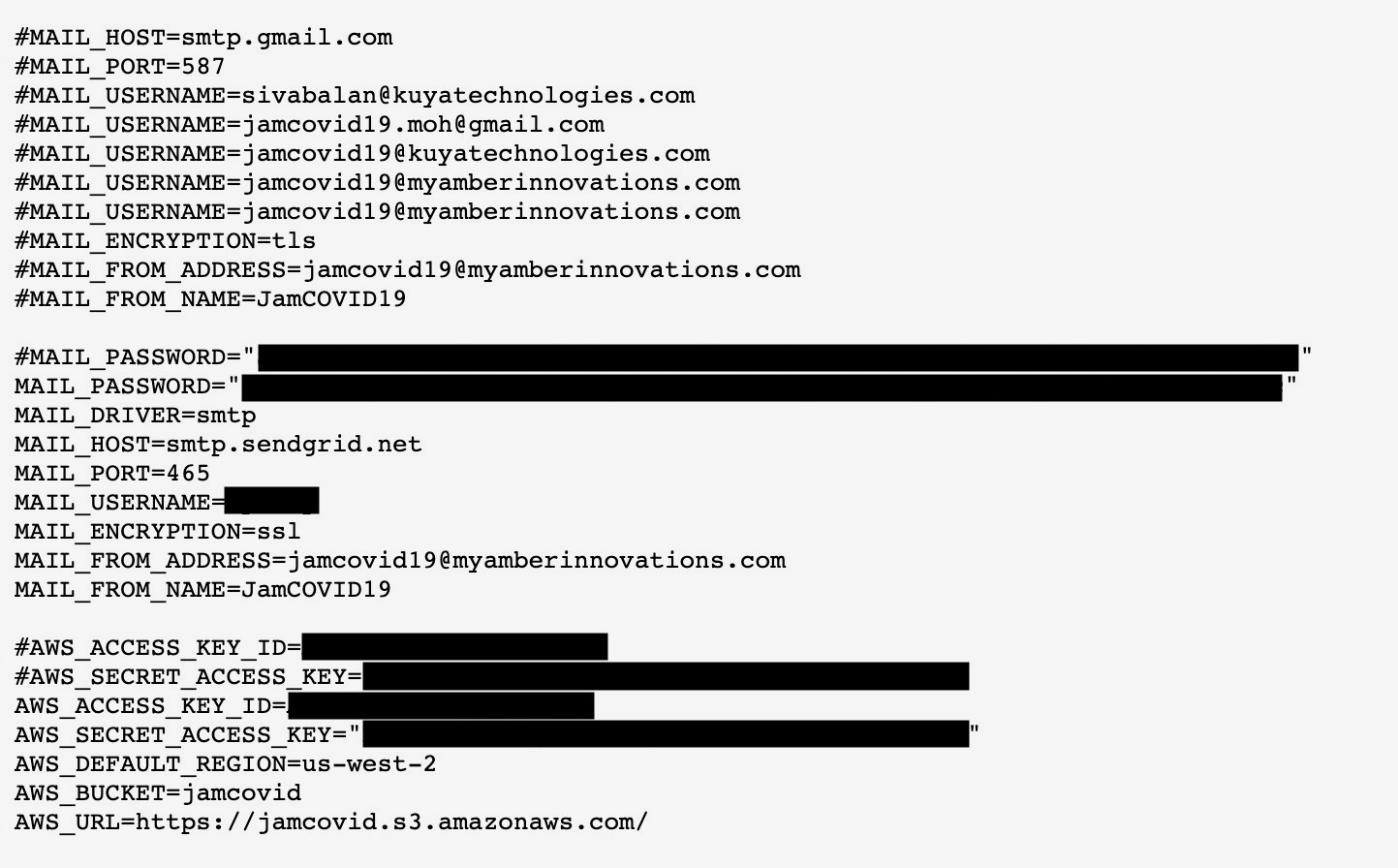
A security researcher told TechCrunch on Sunday that the Amber Group left a file on the JamCOVID website by mistake, which contained passwords that would have granted access to the backend systems, storage, and databases running the JamCOVID site and app. The researcher asked not to be named for fears of legal repercussions from the Jamaican government.
This file, known as an environment variables (.env) file, is often used to store private keys and passwords for third-party services that are necessary for cloud applications to run. But these files are sometimes inadvertently exposed or uploaded by mistake, but can be abused to gain access to data or services that the cloud application relies on if found by a malicious actor.
The exposed environmental variables file was found in an open directory on the JamCOVID website. Although the JamCOVID domain appears to be on the Ministry of Health’s website, Amber Group controls and maintains the JamCOVID dashboard, app, and website.
The exposed file contained secret credentials for the Amazon Web Services databases and storage servers for JamCOVID. The file also contained a username and password to the SMS gateway used by JamCOVID to send text messages, and credentials for its email-sending server. (TechCrunch did not test or use any of the passwords or keys as doing so would be unlawful.)
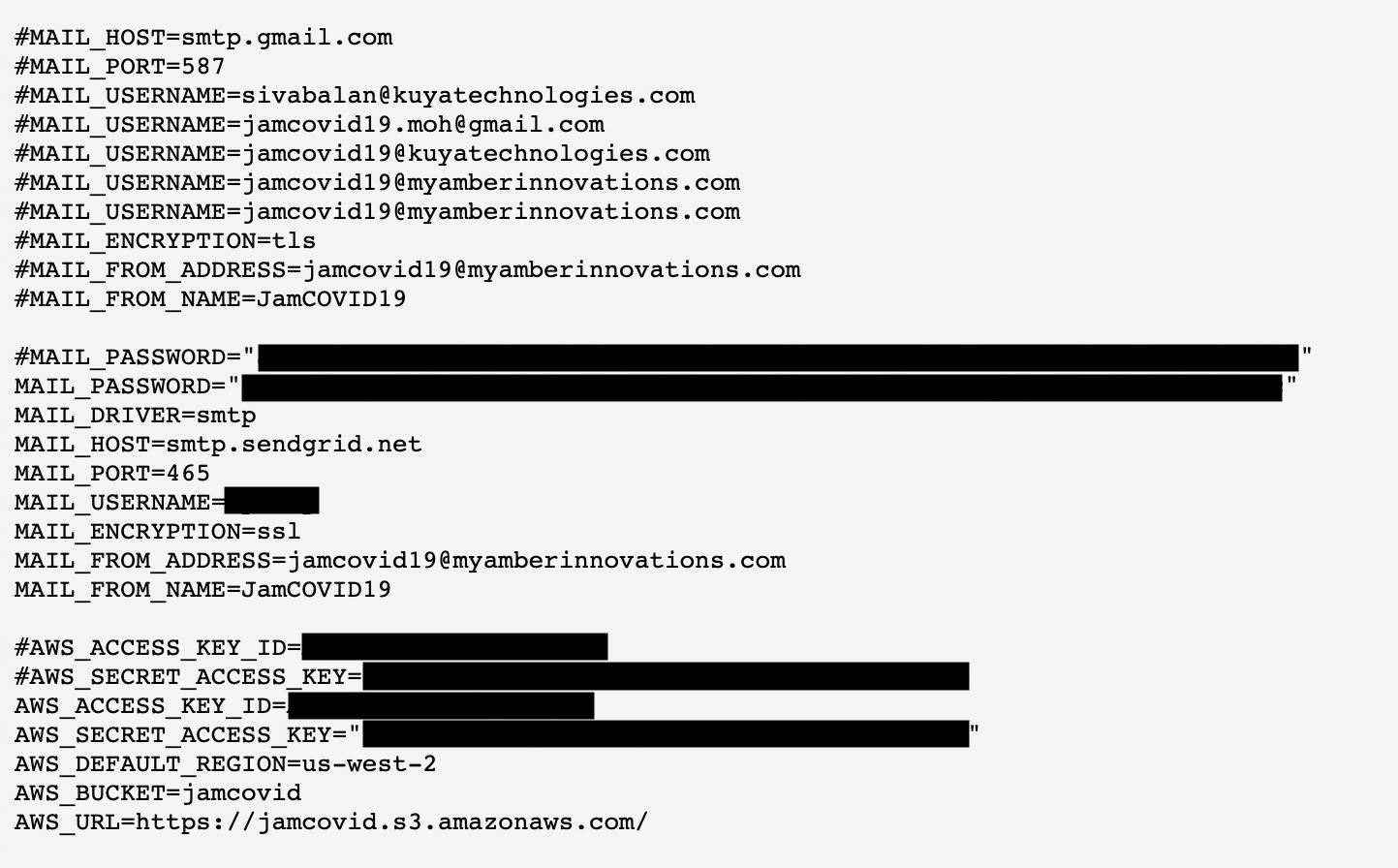
A portion of the exposed credentials found on the JamCOVID website, controlled and maintained by Amber Group. (Image: TechCrunch)
TechCrunch contacted Amber Group’s chief executive Dushyant Savadia to alert the company to the security lapse, who pulled the exposed file offline a short time later. We also asked Savadia, who did not comment, to revoke and replace the keys.
Matthew Samuda, a minister in Jamaica’s Ministry of National Security, did not respond to a request for comment or our questions — including if the Jamaican government plans to continue its contract or relationship with Amber Group, and what — if any — security requirements were agreed upon by both the Amber Group and the Jamaican government for the JamCOVID app and website?
Details of the exposure comes just days after Escala 24×7, a cybersecurity firm based in the Caribbean, claimed that it had found no vulnerabilities in the JamCOVID service following the initial security lapse.
Escala’s chief executive Alejandro Planas declined to say if his company was aware of the second security lapse prior to its comments last week, saying only that his company was under a non-disclosure agreement and “is not able to provide any additional information.”
This latest security incident comes less than a week after Amber Group secured a passwordless cloud server hosting immigration records and negative COVID-19 test results for hundreds of thousands of travelers who visited the island over the past year. Travelers visiting the island are required to upload their COVID-19 test results in order to obtain a travel authorization before their flights. Many of the victims whose information was exposed on the server are Americans.
One news report recently quoted Amber’s Savadia as saying that the company developed JamCOVID19 “within three days.”
Neither the Amber Group nor the Jamaican government have commented to TechCrunch, but Samada told local radio that it has launched a criminal investigation into the security lapse.
Send tips securely over Signal and WhatsApp to +1 646-755-8849. You can also send files or documents using our SecureDrop. Learn more.